Detection
Each client has attack detection software installed on their websites. When a site is attacked, we're alerted immediately.

Analysis
Each attack is analyzed to confirm it is a real threat. Our team checks reporting databases, and does a threat assessment to ensure the attack isnt a 'false positive".

Blocking
Once investigated, the IP Address or entire CIDR is added to our master block list. This process takes less than a few minutes in most cases.

Syndication
Our proprietary system then syndicates our master block list to every server in our network. If one client is attacked, all are protected.
The Most Secure Web Hosting
Hacker Blocker Hosting is a web hosting company that utilizes the Hacker Blocker Firewall Updater System to keep hackers off your website, increasing site speed and performance. Our packages include our proprietary Firewall, detection software, and reporting systems to protect your website from hackers, spammers and bad bots. Our powerful VPS servers are fast, have 99.999% uptime and all the bells and whistles you expect from VPS Hosting.
What is "Hacker Blocker"?
Hacker Blocker is a firewall updating service we created to protect multiple servers from a single attack. When one website or server is attacked, our experts analyze and add the offending IP or CIDR to our firewall. Our firewall is syndicated to all of our servers, keeping all clients protected. With thousands of websites under our protection, our network spans the entire United States and is growing every day.
Websites that switch to Hacker Blocker Hosting see as much as a 300% increase in site speed, and significant drops in spam.
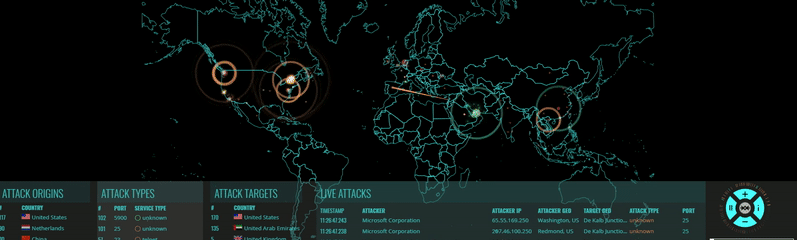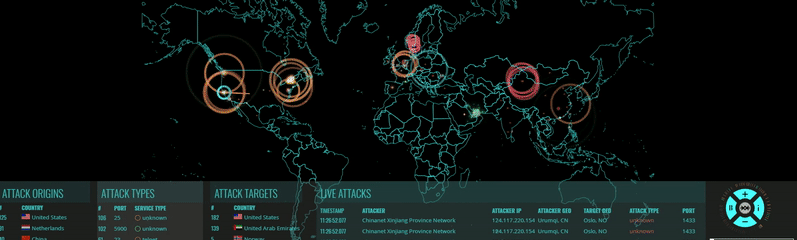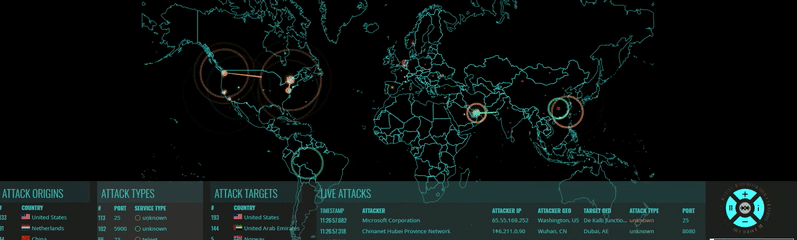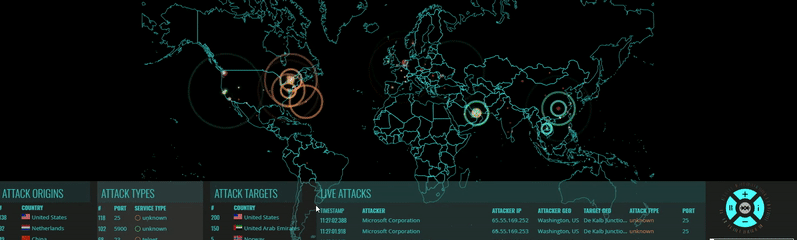
Millions of Hacker IPs Blocked
Hacker Blocker Firewall detects and blocks attacks on any of our client's websites. When one client is attacked, the attackers are blocked from all of our clients, instantly. The result: The more they attack us, the stronger our protection becomes.
Optimized for WordPress and Joomla CMS
Our VPS servers are configured for maximum performance for any CMS, with features like PHP7 & 8, MySQL 5 and advanced caching options to speed up database-driven websites. Clients that transfer to our hosting see as much as a 300% increase in site speed!
Fully Managed Hosting
Hacker Blocker Hosting takes care of everything from setup of your server to migration of your data. We update your server's Operating Systems, cPanel and WHM versions, and can even handle your CMS updates. This frees up your time to do what you do best - run your business.
Dedicated Hosting Updates
Subscribe to our Dedicated Hosting Updater service and get our blocklist syndicated to your Dedicated Server wherever it's hosted. Contact our offices for more information.
How Our Block List is Compiled
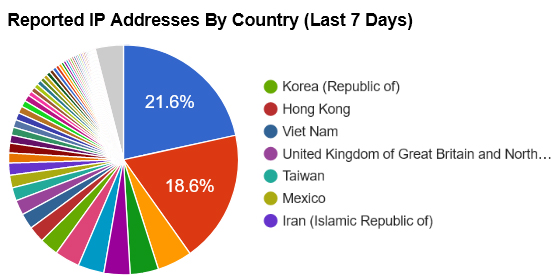 Every day, websites, servers and PC are attacked by hackers and spammers. These cyber-criminals, 90% of them from overseas, continually bombard us with all types of attacks such as Brute Force attacks, Malicious User Agents, Virus Uploads, File Inclusions and plain-old identity theft.
Every day, websites, servers and PC are attacked by hackers and spammers. These cyber-criminals, 90% of them from overseas, continually bombard us with all types of attacks such as Brute Force attacks, Malicious User Agents, Virus Uploads, File Inclusions and plain-old identity theft.
We've created a system that reports attacks on websites and servers across the country to our central station; we then research their origin and if they are a hacker, add their IPs to our block list. Part of our research involves vetting these IPs with online reporting agencies, some of which we've partnered with to import their IP list into our database. This list is consolidated and exported from our Firewall daily, formatted into various file types, and made available to our subscribers. Our block list changes daily, as new IPs are reported, vetted, reviewed and added by our dedicated team. Every one of the IPs in our list are proven Hackers, Spammers and 'Bad Bots'.
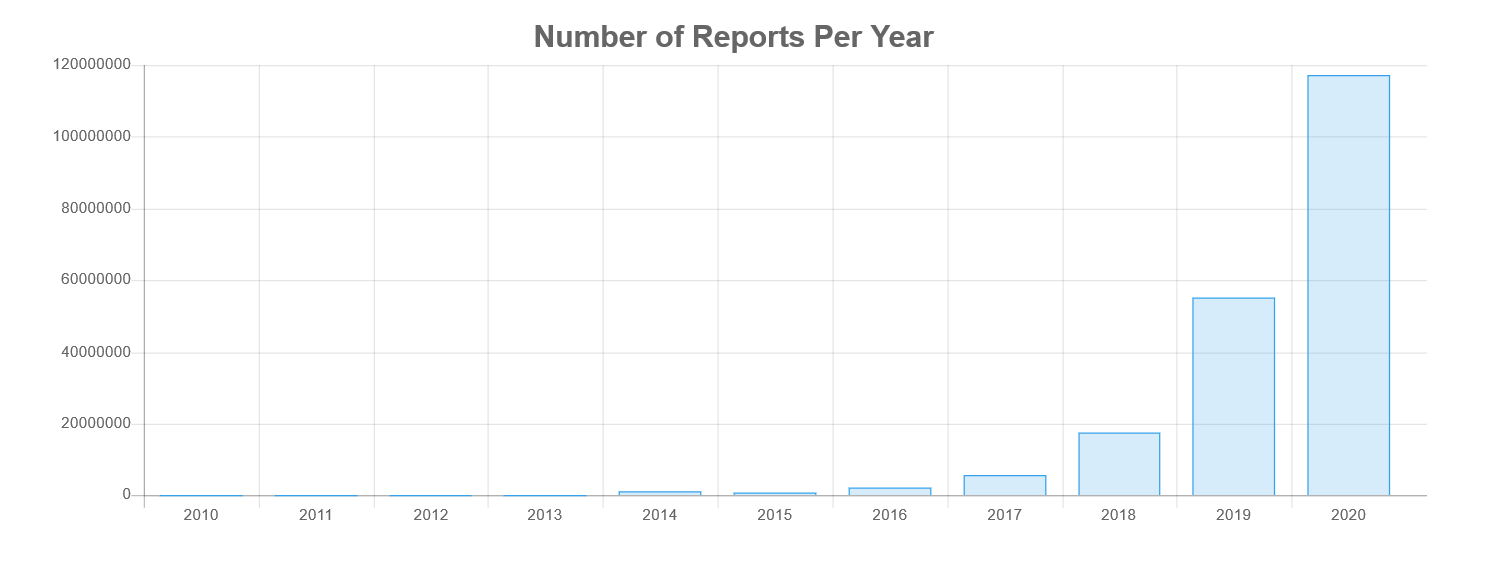
Attacks On The Rise
Each year, more attacks come our way. As hacker networks compromise websites and public-facing servers, they grow larger and the result is an increase of attacks. Businesses cannot wait until they are compromised to take action; today's businesses must be proactive to stay ahead of the competition and hackers.
Call us at +1(617) 819-5877